
According to a 2017 report on application security published by Cybersecurity Ventures, developers generate over 111 billion lines of software code every year. With more developers entering the software industry, the deluge of code continues to increase over time. From a security perspective, this means we have a whole lot of code that should be tested and secured before it reaches the production environment. Otherwise, it poses a lot of risk to individual users, businesses, and governments all over the world.
The U.S. Department of Homeland Security (DHS) published a software assurance report that estimates up to 90 percent of security incidents stem from exploits against defective code and vulnerable software. This is a major point of concern because a broad spectrum of commercial applications and network infrastructure depends on the security and reliability of software products. Unsecure code can put intellectual property, consumer trust, business operations, and organizational services at risk.
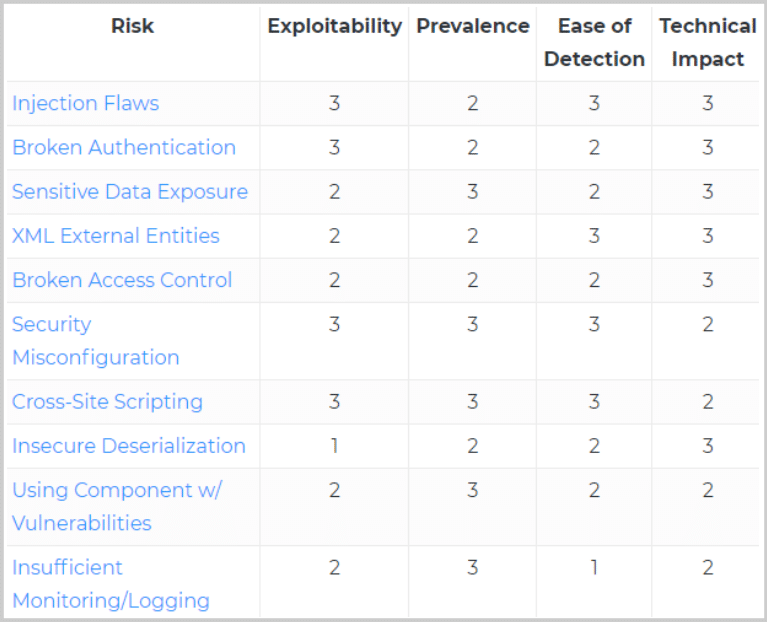
- Exploitability– How easily can an attacker use code vulnerabilities to their advantage (1: Hard to Exploit, 3: Easy to Exploit)
- Prevalence– How common an attack vector or vulnerability is used (1: Uncommon, 3: Widespread)
- Ease of detection– How easily can threats to this attack vector be recognized (1: Hard to detect, 3 Easy to detect)
- Technical Impact– Level of technical damage the attack can cause (1: minor impact, 3: major/severe impact)
Evaluating the risks
Unsecure code is undermining critical systems used in the financial, educational, healthcare, energy, and defense industries and beyond. As software applications become more complex and connected, maintaining a high level of security grows exponentially more difficult.
Nevertheless, no matter how rapid-paced and highly demanding today’s software development environment is, we should resolve security problems as they prose greater risks to businesses.
The Open Web Application Security Project, commonly known by its OWASP acronym, put together a list of top ten risks posed by unsecure code. Their 2017 report on ten of the most critical web application security risks, dubbed as OWASP Top 10 – 2017, clearly demonstrates that the cost of unsecure code is enormous.
From broken authentication to sensitive data exposure and injection flaws to broken access control, unsecured code poses significant risks to application security.
OWASP gathers this data from hundreds of organizations across the globe and over 100,000 applications and APIs.
Below are the main security risks as per the OWASP Top 10 – 2017. These risks are analyzed in four main security dimensions namely:
em all.
- Exploitability– How easily can an attacker use code vulnerabilities to their advantage (1: Hard to Exploit, 3: Easy to Exploit)
- Prevalence– How common an attack vector or vulnerability is used (1: Uncommon, 3: Widespread)
- Ease of detection– How easily can threats to this attack vector be recognized (1: Hard to detect, 3 Easy to detect)
- Technical Impact– Level of technical damage the attack can cause (1: minor impact, 3: major/severe impact)
Worth a mention is that unsecure code not only poses a threat to web applications but also mobile devices. With the growing usage of mobile devices, vulnerabilities associated with mobile applications have also been on the rise.
In November 2019, NowSecure, a leading mobile security company, tested 250 widely used apps on Play Store and found that nearly 70% of the apps leaked user credentials and other sensitive personal data.
According to Kaspersky, the company’s in-lab detection technologies processed over 360,000 malicious files every day in 2017. Out of these files, 78 percent were malware programs, mainly targeting mobile devices.
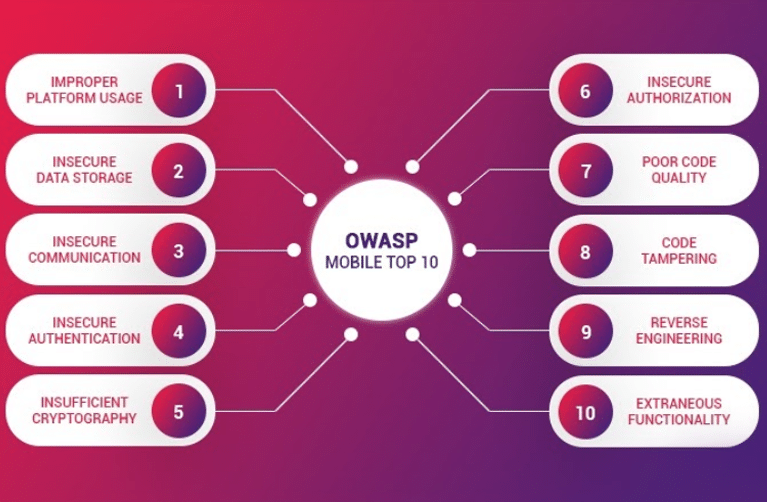
OWASP also put together the top 10 security risks in mobile applications.
Alarmingly, NowSecure found that 85 percent of the apps tested are affected by at least one of these mobile security risks. With these figures, it is inherent that insecure coding poses a major threat to mobile application usage.
Unsecure code compromises personal, business, and government data
Modern software is powerful enough to control complex supply chains, serve as the lifeblood of every social network, and even get astronauts to space and back. Simply put, code has the potential to run the world.
However, malicious code has the potential to do even greater harm and organized crime. From ransomware attacks to data breaches and compromised financial information – the list of cyber-attacks is endless.
Over the years, severe hacks, data breaches, and cyber-attacks have affected millions of users and put billions of dollars at stake. Some include:
- October 2013 Adobe data breach – Affected 153 million customer credit card records and login data
- July 2017 Equifax Data Breach – 147.9 million users affected and their personal information including social security numbers leaked
- May 2019 Canva – Around 137 million user accounts compromised and personal information leaked
- May 2014 eBay – The attack exposed eBay’s entire account list of over 145 million users.
- March 2008 Heartland Payment Systems – Around 134 million credit card details exposed through a denial of service attack
- 2012 and 2016 LinkedIn breaches which leaked social account details of over 165 million users
- 2014 to 2018 Marriot International – Attack went unnoticed for years, exposing over 500 million customer account details
It is essential for the developer community to know that security is critical when building software, just like safety is key when building aircraft. The best approach would be building security into all steps of the software development and quality assurance processes.






