Web applications are subject to a great number of security threats these days and, as a developer, it’s up to you to prevent them from jeopardizing the normal operation of your client’s businesses. Fortunately, when it comes to improving the security of your projects you don’t have to start from scratch – far from that. The security of your webapp can be increased using different approaches, all of which, when combined, result in really robust products.
In this post you’ll learn about 7 resources you can start implementing today to make your PHP applications more secure.
Code Libraries
The first angle you want to apply is to try your best at building security into your coding practice.
In order to do that, you want to be very familiar with the most common vulnerabilities found in php applications and how to prevent them. In addition, a lot of packages and libraries are available for you to improve the security of your applications while writing them.
Here are a few examples:
Secure Headers
First of all, you need to take into account the fact that your PHP applications, at least those that are web-based, are based on the HTTP Protocol. This means you need to be aware of other, somewhat less visible aspects of client-server communication. In particular, there’s a lot of behind-the-scenes information exchanged on the HTTP headers.
Using this simple package, you can make sure the content sent to the client includes directives for secure communication.
Baking this package into your project is rather easy, all you need to do is the following:
1. Add it to your composer.json file.
composer require bepsvpt/secure-headers
2. Copy the headers definition file to its appropriate location.
cp vendor/bepsvpt/secure-headers/config/secure-headers.php .
3. Add the following code before sending content back to the visitor.
And that’s it!
To better see the effect of this, take a look at the response generated by an application not using the package:
curl -v http://localhost:8000/test.php
Will produce this output:
And compare it to one using it:
There are more details you may need to know in order to make the best use of this package. Learn about them here.
PHPSecLib
This library provides PHP implementations of, among others:
- SFTP
- SSH
- AES/CHACHA20/ETC
- X.509
- RSA/DSA/Elliptic curves
PHPSecLib can be installed using composer:
composer require phpseclib/phpseclib
And used like this:
To get a result like:
Of course, there’s much more than simple ssh to be done using this library, take this as starting point.
PHP-Encryption
This library can be used to prevent sensitive data from falling into the wrong hands should a security breach happen.
It’s very important to understand that it’s not intended to be used as a replacement for built-in functions such as pasword_hash and password_verify since this is not a hashing library but an encryption one.
In order to use the library, you must first generate your encryption key by running the following command:
And save the output to some configuration file which has restricted permissions.
Then when you need to use it, you’ll use code similar to:
Which produces this output:
Static Analysis Tools
A complementary approach is to look back once your code is functional and check for potential security risks. In order to do that in an efficient way, you want to take advantage of static analysis tools. Static analysis refers to the practice of asserting whether an application complies with a set of requirements without actually running it, meaning, simply by looking at its code.
Let’s look at some examples.
SonarPHP
SonarPHP is a plugin for the popular SonarQube platform.
Its installation can be a little complex (especially if you have to start from scratch), but once it’s up and running, things can get really interesting.
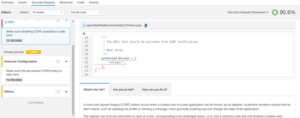
Then, if you want to drill down, you’ll get a lot of useful and detailed information about where the problem is, what are the potential risks your application is exposed to, and what you can do to mitigate them:
Exakat
Exakat is a static analyzer engine for PHP. Besides scanning for vulnerabilities, it can give you hints on other quality aspects of your code. Similar to SonarQube, this is not a library you’ll add to your composer.json file, but rather an external tool that can be downloaded and installed on your computer or used online.
Here’s an example of what running a local instance looks like:
First you need to create a new project like this:
php exakat.phar init -p $PROJECT_NAME -R $GITHUB_REPO_URL;
Then you need to actually run the audit:
php exakat.phar project -p $PROJECT_NAME
Once the audit process is finished, you’ll end up with a report at:
$EXACAT_HOME/projects/$PORJECT_NAME/report/index.html
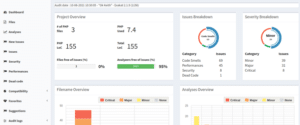
Which looks like this:
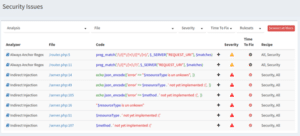
From there you can navigate to the Security Issues section to find more details:
Exakat is an extremely customizable tool and it can take a while to make the most out of it, so the sooner you start, the better.
Security Advisories
Finally we have yet another approach to improving the security of your applications, which is to constantly be monitoring the different vulnerability databases for new threats.
As you may be thinking, there are tools that help make this process smooth and easy.
RoaveSecurityAdvisories
This library is installed via composer as a development dependency:
After installation, it automatically runs on every new composer require or composer update call as a filter for which packages can be added to your project, effectively preventing you from accidentally bringing in vulnerable packages.
Pretty neat, isn’t it?
Local PHP Security Checker
Another tool that aims to provide a similar service is the Local PHP Security Checker.
You can install it by downloading it from GitHub as a binary file, renaming to local-php-security-checker and giving it execution permission.
Once all of that is taken care of, you can simply call it inside your project’s directory, and it will produce an output similar to:
Conclusion
As you can see, many tools out there can significantly increase the security of your PHP applications, most of them are free and open source.
It’s true: It takes some time to get to know all of them, but you probably don’t need every single one. Just go ahead, try them out, pick one of each category, add them to your development workflow. Soon you’ll be able to ship much higher quality products with little effort.






