
It is one thing to know what malicious users will do to your application, it is another to run their tricks and techniques on your own developments. OWASP ZAP — or Zed Attack Proxy — is an open-sourced tool that lets you test the robustness of your application against vulnerabilities. But what exactly is OWASP ZAP?
In a nutshell, it is a penetration testing tool that aids developers and security professionals with detecting and discovering vulnerabilities within a web application. You can do a variety of tasks through OWASP ZAP, including passively scanning web requests, use dictionary lists to find files and folders on a web server, and spider crawl sites to find all the links and URLs. In addition to this, you can intercept, view, modify, and forward web requests between the browser and web application using OWASP ZAP.
An OWASP ZAP scan can reveal issues relating to SQL injection, broken authentication, sensitive data exposure, broken access controls, security misconfigurations, Cross-Site Scripting (XSS), insecure deserialization, components with known vulnerabilities, and any missing security headers.
In this piece, we will go over how OWASP ZAP works, how to set up ZAP, how to create our own spiders to run active scanning.
How Does OWASP ZAP Work?
OWASP ZAP is ultimately a proxy server that scans all the traffic that runs through it. This proxy server consists of auto canners that let you intercept vulnerabilities on your website and produce reports from its findings. Here is a quick diagram of how ZAP works.
ZAP creates its attacks by running the ZAP browser on a URL. During this, ZAP will use its spiders to crawl through a target app, scan all the pages available, then run the active scanner on it. The active scanner will pinpoint any vulnerabilities using known attack methodologies on the targets it gets back from the spider results. Alerts will throw if potential vulnerabilities are discovered and are flagged from high to low based on risk level.
Setting Up ZAP
Here is a quick step-by-step guide on how to set up OWASP ZAP on your computer.
- To set up OWASP ZAP, you need to first install the installer. This is accessible here: zaproxy.org/download Select the installer that is compatible with your operating system.
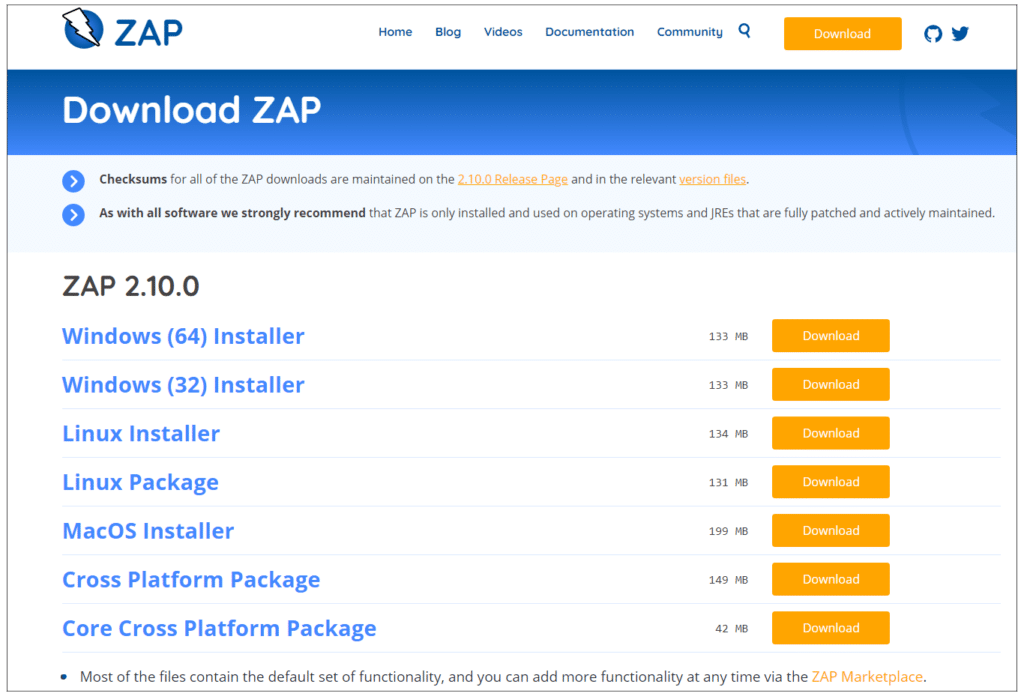
2. Once downloaded, run the installer.
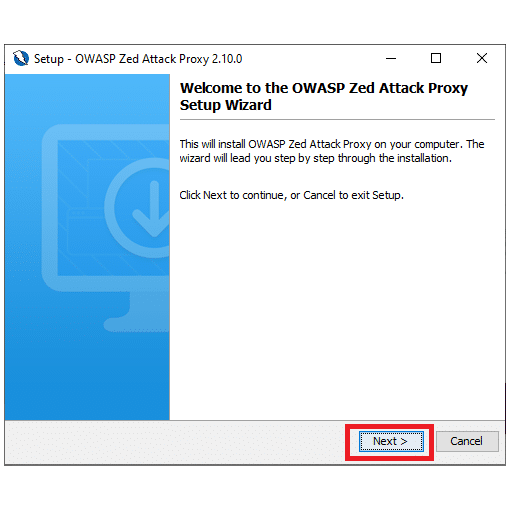
3. Read and accept the terms and conditions in order to proceed.
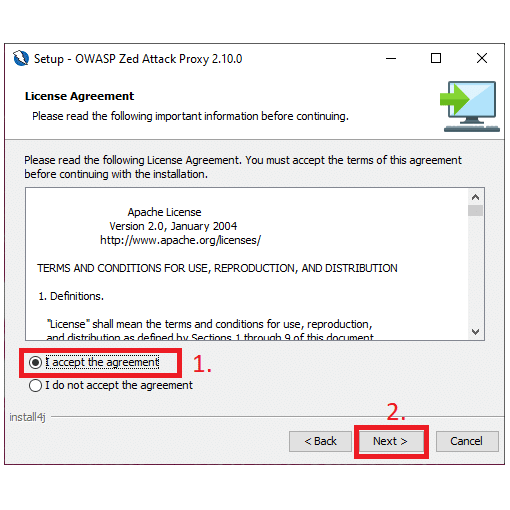
4. Select ‘Standard installation’ as the installation type.
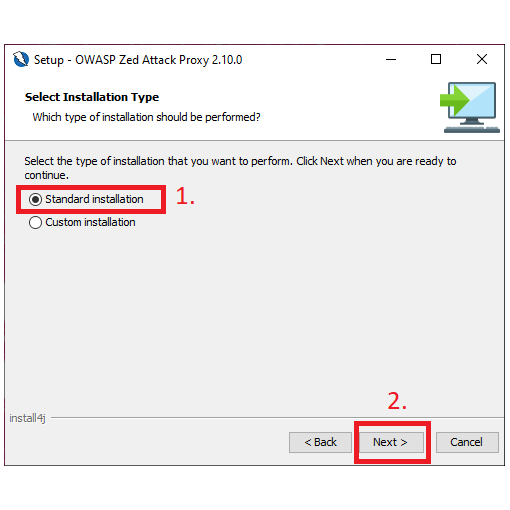
5. You will be given an overview of the installation. Click on ‘Install’ to complete the installation.
6. Here is what your installation screen will look like.
7. Once completed, you will be directed to a screen that looks something like this.
Creating a ZAP Spider
To run your first scan, run your newly installed OWASP ZAP. You will be greeted with a screen that looks something like this:
Once loaded, you will be given a screen that looks something like this. In the main ‘Quick Start’ view, you can select between ‘Automated Scan’ and ‘Manual Explore’. For this tutorial, select ‘Automated Scan’.
This will give you a page that looks something like the below screenshot. You can run it against your application by pointing the target URL to the localhost that your app is currently running on.
Here is an example of what it looks like when it is in the scanning phase.
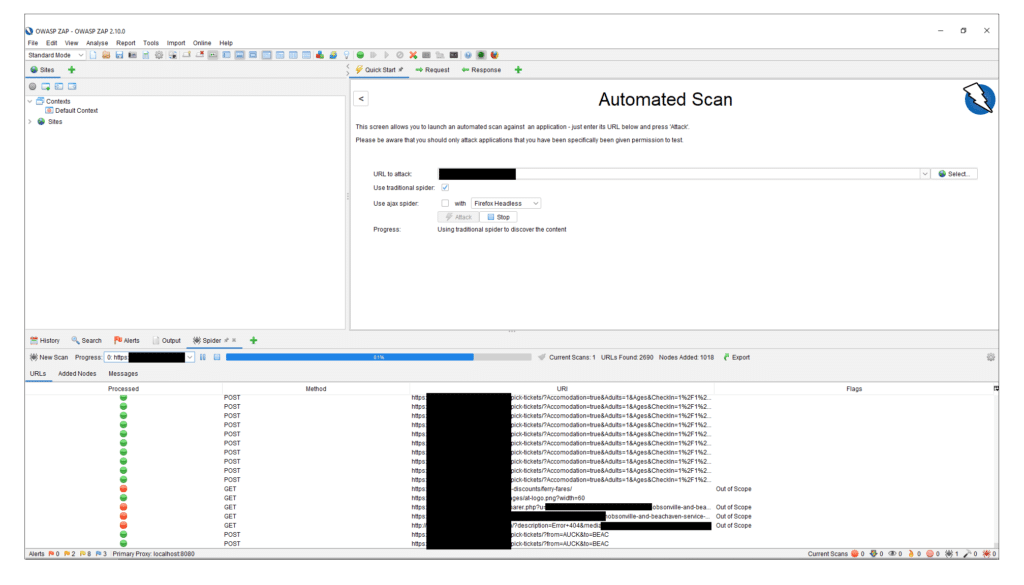
Once completed, you can click on the ‘Alerts’ tab to view all the potential vulnerabilities.
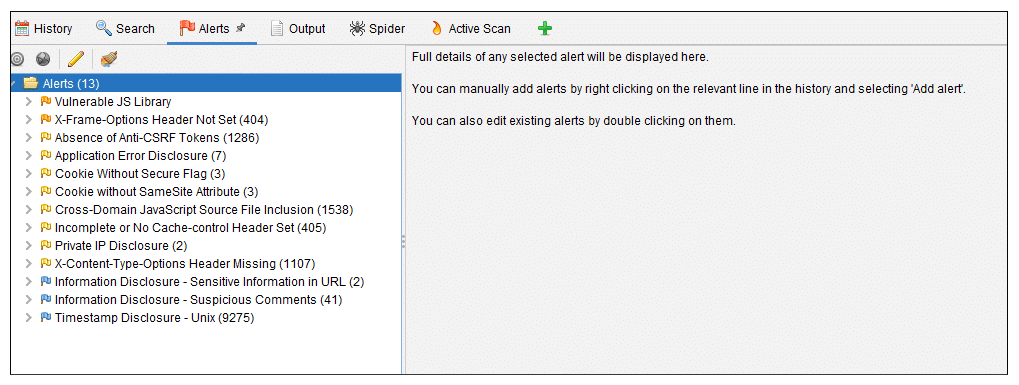
Based on the above scanning result example, we can see that the issues discovered are not critical and easily fixable such as setting the X-Frame-Options header and setting Anti-CSRF Tokens.
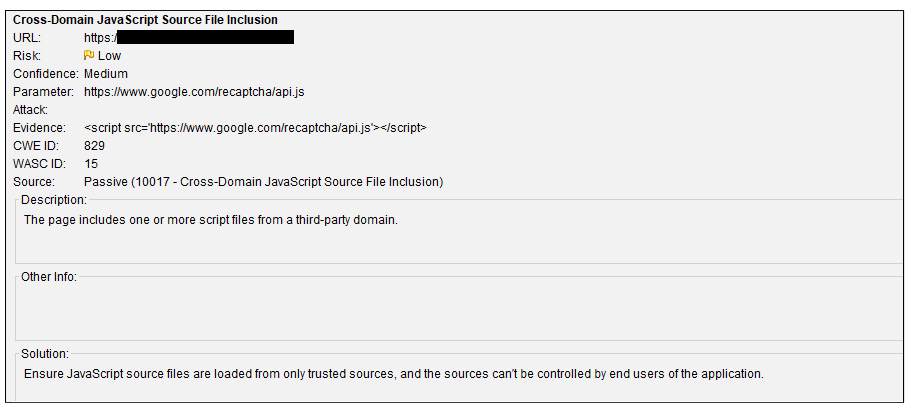
The surface area of a vulnerability can be gauged by the number of instances present for a particular alert. For example, the cross-domain JavaScript source file inclusion appears to be something that occurs through this particular site. However, if we explore further, we find that the risk is classed as low because the source of the a trustworthy one.
Here is a screenshot of one of the flagged alerts and the generated report for Cross-Domain JavaScript Source File Inclusion. Right at the bottom is a solution on how to decrease the vulnerability based on the alert type.
In contrast, if we want to start our vulnerability audit based on severity, OWASP ZAP automatically ranks it for us from highest to lowest in the ‘Alerts’ file list. If we look at the top alert in the generated list for this particular target site, ‘Vulnerable JS Library’ sits at the top. The report is marked as a medium risk because the jQuery used is not the latest version.
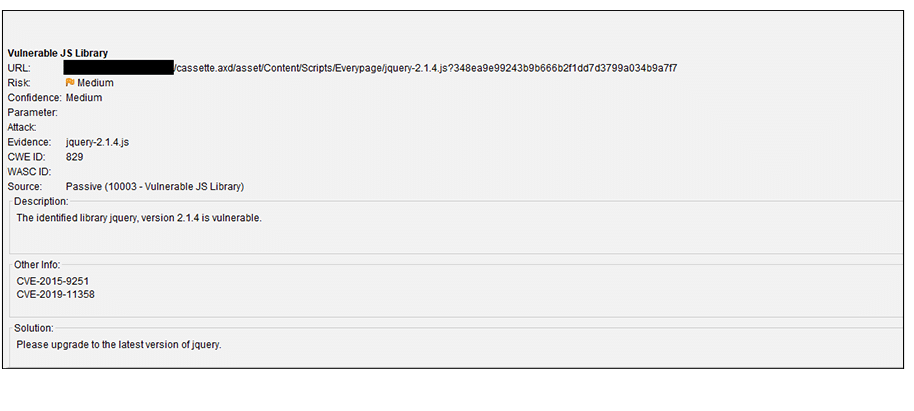
A little search further into jquery-2.1.4 lets us know that this target site is vulnerable to potential Cross-site Scripting (XSS) via <option> elements from untrusted sources, even after sanitization. This is because in this particular version of JQuery, DOM manipulation methods may execute untrusted code.
This illustrates that something that appears seemingly insignificant at first can lead to a larger security vulnerability that may not, at first, be obvious.
Conclusion
OWASP ZAP Quick Scan functionality will not ‘hack’ your application for you. However, it will give you a quick overview of potential issues and vulnerabilities that you may not be aware of in your application.
Running OWASP ZAP during the development phase can also help us improve our security workflows by identifying issues before they grow too big over time. It is easier to fix a potential vulnerability when it is small than when it is big and permeating throughout the entire developed app.
One thing to keep in mind is that if you run OWASP ZAP against a more mature application with a lot of legacy code, you may end up with a large number of alerts and alarms. This is expected and normal, especially if security was not initially part of the development mindset or implemented as a policy. As long as you prioritize your vulnerabilities and work through resolving them, it should increase the robustness of your app.
In addition to running the Quick Scan functionality manually each time, you can also automate it into your workflow either through Docker Packaged Scans, GitHub Actions, or automation frameworks. These are good spaces to explore further if you want to leverage OWASP ZAP for your development workflows.






