
A bug bounty program is a crowdsourcing initiative that is offered by a large number of organizations and websites all around the world. In this initiative, individuals are rewarded with recognition and compensation also called bug bounty for reporting critical flaws in software, especially those that can risk security exploits and vulnerabilities.
Bug bounty programs allow developers and white hat hackers to discover and report software vulnerabilities before the general public using the platform is aware of them. This prevents potential exploitation or widespread abuse of the system.
Today, most of the tech giants, including but not limited to Google, Mozilla, Microsoft, Facebook, Reddit, and Square, are implementing bug bounty programs.
So, now the primary problem is, how to get started with this for your own organization?
Monitoring JavaScript files
With traditional server-side applications, it is very easy to keep track of logs and bugs, but with a client-side application, things are a bit different. JavaScript is one of the most popular technologies that is used to build modern-day applications for modern web browsers.
The front-end of the applications is developed using client-side JavaScript frameworks such as Angular, React, and Vue. These drive a lot of functionality and logic for the front-end, therefore flagging the way for enhanced attacks and vulnerabilities.
In order to find vulnerabilities in a target, a static analysis of client-side JavaScript is performed. This procedure leads to some or all of the following outputs
- URLs, domains, etc which can cause possible exploits.
- Sensitive information, like authentication credentials, secret keys to APIs, storage, etc
- Potential wildcard entries
- Any outdated or old frameworks with known vulnerabilities.
Fortunately, there are many free and open-source tools available to extract all the above information on your desired target.
ScriptHunter by Robre
This tool, written by Robre, is a simple script that is really very helpful in finding the javascript files in a web application.
This tool has a dependency on a couple of other tools, which are written in Go language. So before installing and configuring the following tools, you’ll have to install and configure Go properly. These tools are:
This tool first runs getallurls (gau) to search for javascript files from public sources for your target domain. Then, to find JavaScript files that are embedded in the websites code, i.e. mentioned in the script tag, scripthunter runs hakrawler.
Next, using the result of the previous step, a list of directories is extracted, which contains the JavaScript files. All of the directories recorded is then examined using ffuf, with a custom wordlist.
The output the whole process looks like following
Bug-Bounty-Toolz
After collecting the JavaScript files, the next step is to extract something meaningful out of them. To do this, we can use a tool by GitHub repo, Bug-Bounty-Toolz, which has a simple python script getjswords.py. This goes through all the JavaScript files that were captured using the ScriptHunter tool in the previous step and creates a wordlist containing all the information that is in the JavaScript files.
Next, you take those words and sort them. Now, these words can be used with ffuf as shown below.
JSmon by Robre
A key in bug bounty is to actively monitor the targets. That being said, if any change in the code of JavaScript are deployed on the target system, we would want to receive an alert for that. This is done so that we can immediately get working on new or changed targets and components.
For this purpose, we can use JavaScript Change Monitor for Bug Bounty by Robre. JsMon is an uncomplicated script where you can configure any quantity of Javascript files on your target website that you want to watch. On every run, JSMon script will retrieve your expected files and match them to the previously obtained versions.
It results to find any changed, you will be informed via telegram push notification. This script will calculate the changed file sizes and difference in the files so that you can inspect them easily.
The difference will be shown as follows.
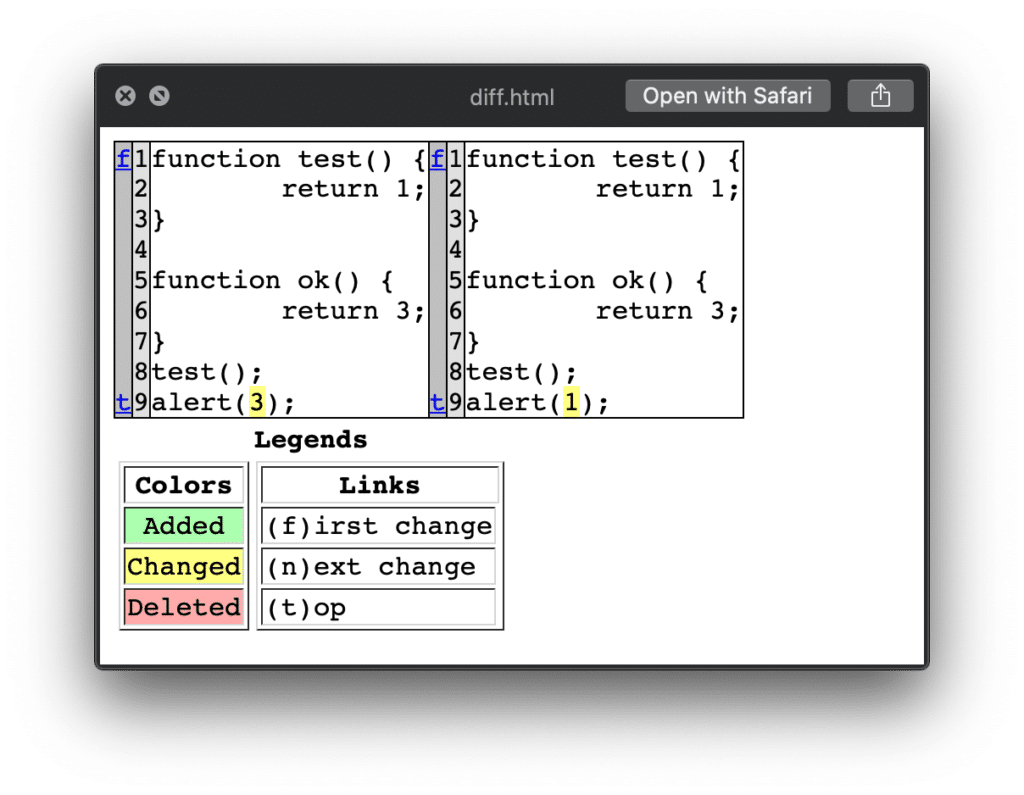
Source: GitHub
Preventing JavaScript Monitoring
In order to prevent others from exploiting our Javascript, we can use an obfuscator to obfuscate the javascript for the readers. The tools that can be used to obfuscate the JavaScript are:
The above tools will minify/compress and analyze the code to find and remove unused code. These tools then rewrite for maximum minification.
Summary
In this article, we’ve covered a generic approach to perform analysis and monitor JavaScript files which are a useful technique in Bug Bounty hunting.
What we have covered is a workflow that takes you from gathering javascript files to finding hidden information and continuous monitoring of JavaScript changes on a target system. This brings us to the end of the article. Have a happy bug hunting!.





