Why is Penetration Testing Important?
Penetration testing attempts to compromise a corporate system. If the system has adequate protection, the test will at least trigger a security alert. Otherwise, the system is considered to be at risk.
When testing is complete, the penetration test report reveals vulnerabilities discovered and exploited. Incident response team must analyze these vulnerabilities, identify which of them represents a significant threat and remediate them immediately. In some cases they may defer action on vulnerabilities that are not critical, while remaining aware of them for the future.
A major benefit of the penetration testing approach is that it enables creativity on the part of the tester. Testers can design a penetration test based on spear phishing messages to a business executive, a brute force attack on a weak password, or select any other threat vector. A creative approach is more likely to result in a penetration test that simulates a real attack.
In most cases, penetration testers are contractors. Many organizations also offer bounty programs, offering certain prizes or fees for ethical hackers who manage to bypass their defenses or identify a bug that has security significance. There is an advantage to having a third party test the organization’s systems, because they operate with similar knowledge to that of external attackers, and are more likely to find security gaps that threat actors are able to exploit.
Let’s review the seven phases of a penetration test in more detail.
What are the 7 Penetration Testing Steps?
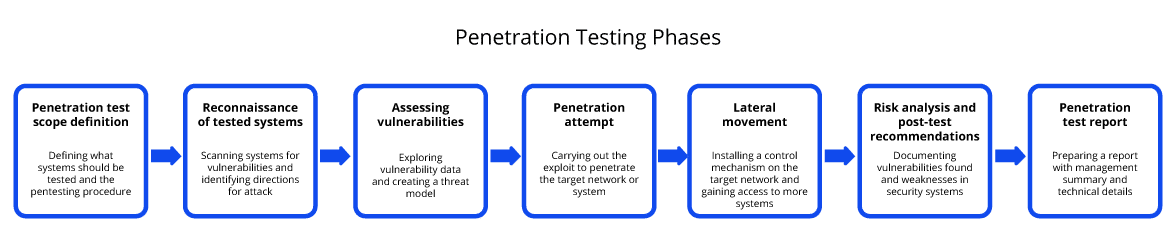
A good penetration testing program includes both automated and manual steps that can test an organization’s security defenses. A comprehensive penetration test should include the following seven steps:
| 1 | Penetration test scope definition | Defining what systems should be tested and the pentesting procedure |
| 2 | Reconnaissance of tested systems | Scanning systems for vulnerabilities and identifying directions for attack |
| 3 | Assessing vulnerabilities | Exploring vulnerability data and creating a threat model |
| 4 | Penetration attempt | Carrying out the exploit to penetrate the target network or system |
| 5 | Lateral movement | Installing a control mechanism on the target network and gaining access to more systems |
| 6 | Risk analysis and post-test recommendations | Documenting vulnerabilities found and weaknesses in security systems |
| 7 | Penetration test report | Preparing a report with management summary and technical details |
The best penetration tests include reconnaissance and careful definition of targets, use automatic scanning tools to find vulnerabilities, and manual verification to select the best ones to exploit. Penetration testers can set up close monitoring of the designated target without disruption to business processes.
Penetration Testing Steps In Depth
1. Scoping
The test scope agreement is usually defined upfront with the penetration test vendor, and should include the testing methods and the level of exploitation allowed when vulnerabilities are discovered. Penetration testing is a white hat process—the attacker is a tester who works according to the rules of engagement established in the scope definition. Therefore, a penetration test should never interfere with normal business operations.
The ethical hacker performing the penetration test can gain access to sensitive insights and information, and must sign a confidentiality agreement before starting the penetration testing process.
2. Reconnaissance
In the reconnaissance stage, the tester attempts to collect as much information as possible on the organization’s systems, potential targets and their vulnerabilities. Penetration testers primarily rely on open source intelligence sources and independent scans of IT systems.
The penetration tester may or may not have access to information about the organization’s internal systems. In some cases, an organization may point the attacker in the direction of specific targets or vulnerabilities they are concerned about.
Some common information gathering techniques are:
- Search engine querying
- DNS or WHOIS lookups
- Social engineering
- Tax records or other public records
- Email addresses, user accounts and social profiles available on the Internet
- Ping probes, port scans, reverse DNS, packet sniffing
- Shoulder surfing, or publically accessible physical locations like dumpsters
3. Vulnerability Assessment
In this step, the penetration tester applies a probe to the target network, collects preliminary information, and reviews the results to investigate directions for exploitation.
This step may result in discoveries like:
- The directory structure of a specific server
- Open authenticated access to an FTP servers
- SMTP access points that provide details about the network architecture through error messages
- Possibility for remote code execution
- Cross-site scripting vulnerabilities
- An internal code-signing certificate that can be used to sign new scripts and inject them into the network
4. Penetration Testing
One the tester has identified the key vulnerabilities they want to exploit, and created a threat model and attack plan, the next step is to penetrate the target system. There is no guarantee that all vulnerabilities found will be exploited in the test, either because they were less convenient for the attacker, or because they are outside the scope of the test.
The main goal of the penetration tester is to find at least one vulnerability that allows them to access the target system, either compromising it or accessing sensitive data. Once inside, the tester will collect more detailed data from the target network to facilitate the next step.
5. Lateral Movement
Like a real advanced persistent threat (APT), once a penetration tester has succeeded in penetrating the security perimeter or compromising a target system, they will install malware or another mechanism to allow continued access. The control mechanism should be persistent and remain on the network even even if the system is restarted or maintained.
Using this foothold in the network, the tester will attempt to reach additional, potentially more sensitive targets. All this while following the agreed project scope and avoiding damage to organizational systems.
6. Risk Analysis, Post-Test Recommendations and Cleanup
Once the penetration tester has completed their activity, they should carefully document the vulnerabilities discovered, what they did to gain access to the organization’s systems or data, and the value of compromised systems to a real attacker.
An important part of a penetration tester’s analysis should be recommendations for closing security gaps found in the environment. The penetration testing vendor should provide an actionable recommendation on remediating any significant vulnerability discovered in the test.
Finally, the penetration tester must perform cleanup of the organization, removing any components they have added to the environment, and removing access or privilege they received.
The cleanup process typically includes:
- Deleting temporary files, executable files, scripts or rootkits from target systems
- Reverting configurations to original settings
- Reverting credentials or access rights to their original state
- Removing new user accounts created for lateral movement purposes
7. Penetration Test Report
Finally, the penetration tester submits a report to the organization. The report should communicate the results of the test to two audiences: management and technical or security teams.
The penetration testing report should include:
- An executive summary—explaining the penetration test strategy in business terms, identifying test results by risk rating. It is intended for the business team, and will be used to make decisions about what to fix, and which issues represent an acceptable level of risk.
- Technical details—which should be descriptive and specific, and can be used by technical teams to take action and fix security issues discovered during the penetration test.
Conclusion
Penetration tests can help you identify security threats. However, to be truly effective, a penetration testing program needs to perform seven key steps. Typically, you start with scoping, during which the tester and organization define their terms of agreement.
This is followed by reconnaissance and a vulnerability assessment, and then the penetration testing step begins. The tester then performs lateral movement activities in the network, followed by a risk analysis and post-test recommendation and cleanups.
During the last step the tester provides a penetration test report, which includes an executive summary and technical details. Automation can be introduced during the majority of the steps, but this is typically a hybrid process that involves both machine and human resources.





