A server is essentially a computer (hardware and software) whose function is to store information, provide services, run programs, and more. Only authenticated users can access a server. However, sometimes a server’s data can be compromised by hackers. To prevent miscellaneous activity, you need to make sure your server is secure, so you need to do some server-level configurations. But before moving forward, let’s understand different types of servers and their functions.
Types of servers
Web servers
A web server’s primary responsibility is to host web programs and user’s data. It gets requests from anywhere across the web. Usually, web servers get the request from web browsers and respond via data. Examples of web servers are Apache and Nginx.
Mail servers
A mail server is for email services. It receives emails from a user, stores them, and sends them back to receivers. Some examples are Gmail, Yahoo, or ProtonMail.
File servers
The primary purpose of a file server is to store and distribute files across the web. When a user shares files via a communication channel, it passes through a file server. It may store the files and send them to the user when a request came.
Apart from this, there are many more types of servers like DNS servers, print servers, virtual servers, proxy servers.
Types of Attacks
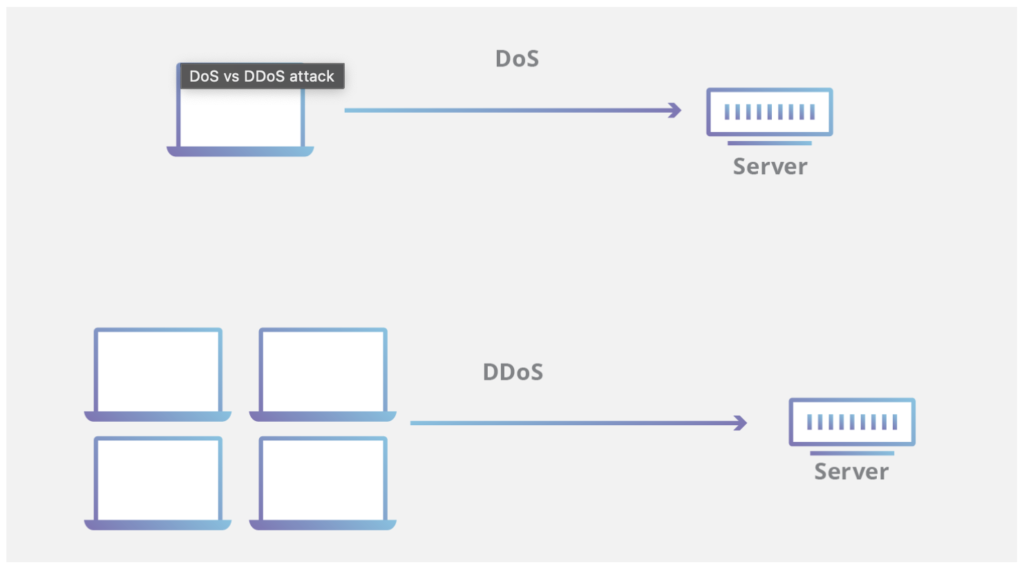
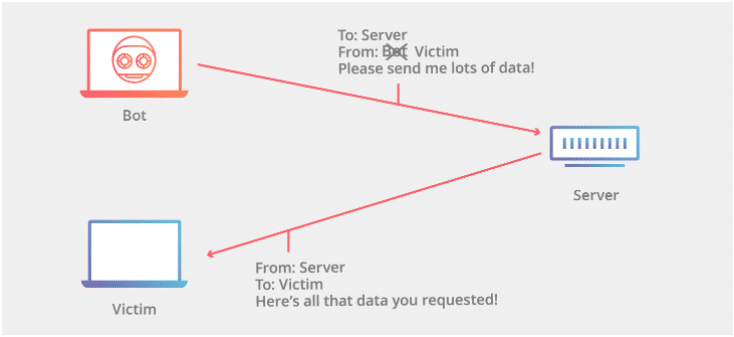
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks
This is the most common attack an attacker can perform. They will send multiple service requests to a server simultaneously so that server is not available for regular users, causing a denial of service (DoS) notification.
The attacker first checks for server vulnerabilities and capacities before performing this attack, as simple coding errors can cause DoS attacks. A DDoS attack is a combination of multiple DoS attacks serving from more than one source/location.
How to Prevent a DoS/DDoS attack?
Configure your servers against DoS/DDoS attacks
Many hardware configurations are available in the market that can help you prevent a DoD/DDoS attack. For example, configure your firewall, which can reject a service request that comes more than twice within timeframes.
Use DoS/DDoS protection hardware
When you purchase a server or build a server, make sure you add good hardware that prevents a DoS/DDoS. Brands like Cisco, arbor, and many more provide hardware that blocks DoS/DDoS.
Purchase higher bandwidth server
The best way to prevent a DoS/DDoS is to purchase a higher bandwidth server, So, when an attacker performs an attack, your server won’t get affected.
SQL Injection Attack
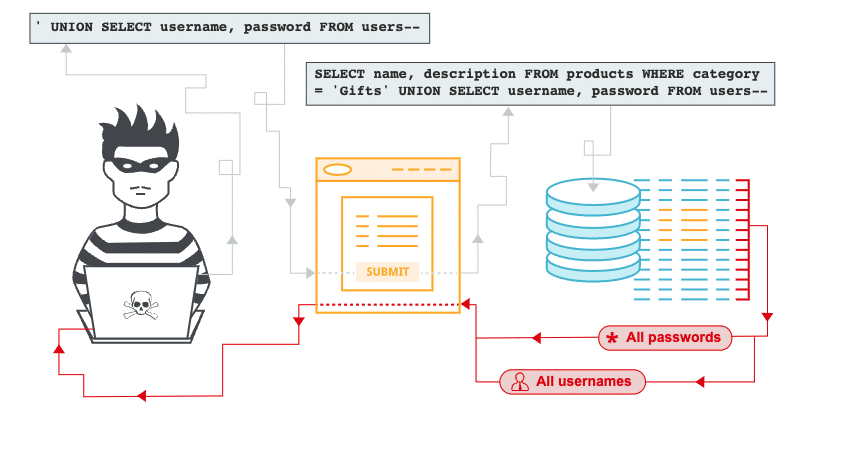
SQL injection is a web application bug that allows an attacker to exploit a database’s information by hitting queries from a user interface. Systems already use queries to perform CRUD (create, read, update and delete) operations. The attacker gets all the data that was not meant to be seen by the end-user by executing a query. An attacker can also change or delete the existing data. That will make a system unstable. Sometimes attackers may change the backend and can also perform denial-of-service attacks.
Let’s understand SQL injection by one example. Consider the login page of any application that will simply take a username and password to enter the web app. When a user clicks on a login button URL will be something like this:
This will be sent to the server to validate a user. So the backend will fire the given query to validate a user.
SELECT * FROM users WHERE username = ‘abc’ AND password = “ijasd”
Let’s assume the application does not have any SQL preventions. So, now instead of actual username hacker write something like abc’+OR+1=1 So, now URL will be like,
This will be interpreted in your backend like below,
SELECT * FROM users WHERE username = ‘abc’ OR 1=1–‘ AND password = “hasbd”
This query will fetch all the data because the additional condition 1==1 will always be valid for all cases. This way attacker can get all your data very easily.
How to prevent SQL Injection?
Input validation
An attacker can get data by entering miscellaneous information in the input boxes. So the base step to prevent this type of attack is input validation. Before sending it to the server, validate the input data and remove unnecessary data like special characters, some conditional data. You can also use regex to whitelist input data.
Stored Procedure
Stored procedures are a coding technique in which a developer puts a group of SQL queries into a single logical unit for future execution. When you need to call the same queries more than once, just put it into a stored procedure and call it whenever you want. It will automatically check the query before any calls.
Avoiding administrative privileges
One should avoid connecting the root user to connect directly to your application database. For this reason, it’s better to connect the one who’s having fewer privileges to the database.
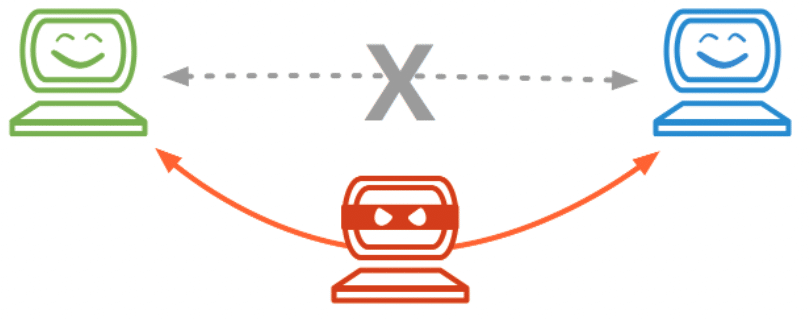
Man-in-the-Middle Attack
A man-in-the-middle attack is a term when an attacker places themselves between a user and a server. They pretend to be the server for the user and a user for the server. No one knows that a hacker is intercepting the conversation. This attack’s primary goal is to get users’ personal details, like passwords, account details, and private messages.
How to prevent a man-in-the-middle attack?
MitM attack can be prevented by following the given steps:
- Use HTTPS websites
- Make sure you log out after your work is done (like after making a transaction on net banking sites)
- Avoid using free Wi-Fi at hotels, malls, or at any shops.
Cross-site Scripting (XSS) Attack
Cross-site-scripting is a type of attack in which hackers inject malicious code into web apps, usually on the client-side. An attacker’s end goal is to run that script on a selected client’s web browser with his trusted websites. After the execution, those sites become the mediator for a hacker.
Eventually, the hacker will access all of a user’s crucial data. A website is vulnerable to XSS attack if a website done’s not sanitize user’s input before sending it to server. This user input is going to parse on a victim’s end. The most typical XSS attack can be done with Javascript because JS is a widely and most commonly used frontend language.
An XSS attack is less dangerous than an SQL injection because an attacker can’t access all the data at once. If an attacker digs a dipper on a browser side, they may access all the Javascript files to change that code or perform XMLHttpRequest to get send or get data from a server.
Let’s check XSS with one example; suppose you want to show a list of products:
<html>
<h1>Products</h1>
<h1> Product 1 </h1>
<h1> Product 2 </h1>
<h1> Product 3 </h1>
</html>
This code executes in a user’s browser when requests come. Now hacker attacks a user’s system by adding one more line to the given code:
<script>HacketsScript()</script>
Now when the user sends a request to the web server, it simply receive the given code. That has hacker’s script.
<html>
<h1>Products</h1>
<script>HacketsScript()</script>
<h1> Product 1 </h1>
<h1> Product 2 </h1>
<h1> Product 3 </h1>
</html>
When this code is executed in the victim’s web browser, the hacker’s script runs too. This way, hackers can manipulate the frontend code.
How to prevent cross-site-scripting attacks
- Filter user input: Sanitize the user’s input when they request some data. You can add a strict filter based on the expected input.
- Use proper request/response headers: The best way to prevent XSS on an HTTP/HTTPS request is to set appropriate headers, like for JSON requests, avoid getting HTML or JS. Use Content-Type:json and same for others.
- Encrypt Input/output: When you encrypt the input and outputs, then there are more chances that a hacker might not understand a user’s data.
Malware Attack
Malware is just a piece of code that executes at the victim’s end and gets all necessary information or may cause severe problems to a system. The primary purpose of injecting malware is to harm a user’s system and get personal details like credentials, payment information, etc.
Types of Malware Attack
- Trojan Horse: Trojan horse is a software/program that a hacker will send to a user in the form of a game or an application. A Trojan Horse depends on a user downloading this file, and then it gets access to the user’s system.
- Virus: It is also in the form of a file; it will get into the user’s system via a different medium, like the internet, or via data transfer. A virus will infect different parts of the user’s system, such as the operating system, RAM, hard drive, or ant applications.
- Worm: If malware self-propagates to another system, it is known as a worm. A worm will damage the user’s system without using it. It propagates without any interactions.
- Malvertising: A hacker will purchase advertisement space, and inside that, they put malware. As soon as the user clicks on it, their system gets compromised, and hackers will access it.
How to Prevent Malware Attacks
Use a secure network
For the first step, use a firewall that blocks unknown requests and files so that users won’t get malware. Apart from a firewall, you can use IPS or IDP. You should avoid using a VPN because your request is routing through multiple routes, and it may increase the chances for attackers to insert malware. An organizer can prevent access or grant only necessary access to a user.
Keep regular backups
It’s essential to keep a periodic backup for a system or database. If your system is compromised, you can immediately remove all the files and restore the backup.
Use the latest software
Software updates are critical because it involves security. A new release comes with resolved identified bugs and may have updated securities.
Scan files before use
When you download any files from the internet or take any files from different hardware, make sure you scan it with an antivirus tool.
Spoofing Attacks
In a spoofing attack, a hacker creates a situation in which their program pretends to be a trusted source by falsifying identity. The primary purpose of this attack is to get illegal access to the user’s system. Spoofing is used to spread malware, obtain personal information, bypass the firewall, and access the system. Spoofing can be through communication, phone call, a transaction, etc. Spoofing can be even deeper, like IP spoofing, Domain Name System (DNS) spoofing, etc.
Types of Spoofing Attacks
Email Spoofing
It’s like pretending to be an authenticated email service. An attacker will send an email from a seemingly trusted source so that the recipient trusts it. In the email, the attacker will request personal information, which the victim will volunteer. The attacker is able to create a convincing email address by copying the original and changing a few characters or numbers (for example, changing lowercase ‘l’ to uppercase ‘I’).
Website Spoofing
It’s similar to email spoofing but the difference is that the attacker spoofs a website (instead of an email address) by making a copy of an original one. The attacker gets a similar DNS to host their website. If a user visits that website then the attacker can potentially receive all the personal details of a user.
Internet Protocol (IP) Spoofing
In this attack, the attacker spoofs the user’s IP with their IP. It is mainly used to access a system which can be accessed by trusted users only. So, hackers spoof an IP and gain access. It is most commonly used for DoS attacks, where attackers will spoof IP of a target system and send multiple requests from all the users.
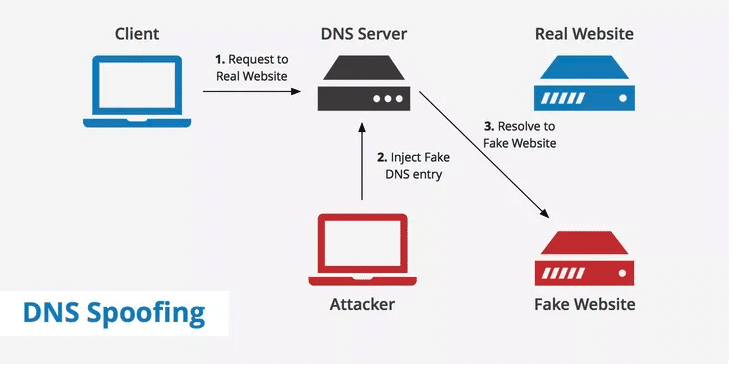
Domain Name System (DNS) Server Spoofing
Here, the attacker spoofs a DNS and binds their IP with it. So, all incoming requests go to an attacker’s website and they can receive all of the victim’s data and also send malware in response.
How to Prevent Spoofing Attack
Spoofing is basically a bit of change in the original name. So, to be safe from spoofing, you need to take care of your email, website, or phone number. Before sending important information, check the sender’s details twice. You must check for spelling, grammar mistakes, improper sentences, special characters, etc. If you identify any of these errors, you can immediately know that this is not the original source.
Don’t open unknown and suspicious websites. If you’re unsure about an email or website, it’s better to just let it go. Don’t share personal information with unknown sources.
Conclusion
To make your system secure, you must understand all the attacks. As demonstrated by this article, attackers can use many different techniques to exploit a server or its data. In order to make your system secure, keeps it up to date with the latest security/software. The most important step is to configure your firewall very well, and only give access to authorized users. You can also configure notification or email updates which signal when your system is compromised so that you can take the necessary steps before it’s too late.