Nowadays, everything is accessible through the internet. Data regarding Personally Identifiable Information (PII), health care, or cardholders require higher levels of protection than regular data. However, protecting all data from attackers is our primary duty.
Since we store our confidential user data in a database, we need a database with several layers of security. If a data breach occurs, depending on the amount or the sensitivity of the data, this could be very problematic. How does a company secure itself against data breaches? Let us discuss some of the solutions one by one.
1. Separate Database Servers
Performance, availability, confidentiality, protection, and reliability are just a few factors that influence server architecture. Keeping all (application server, web server, database server) in one place improves efficiency, but today’s businesses want to protect their users’ data.
As a result, they keep the database separate from the rest of the environment and remove the database server from the DMZ and the public internet. In such an architecture, the database server is not directly visible to the user.
What does a database server do?
Usually, it stores data and retrieves it in response to a user query. Users make a query with the help of the application server. We must attach the application server to the database server and grant the necessary authorization to update, insert, or delete data.
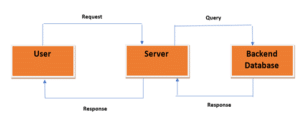
Here, the user sends a query to the server to retrieve information, such as their profile information. The server receives the request and, since the information is saved in the database, sends a request to the database server, asking for the same information. If the database has the information, it sends it to the server, and the server responds to the user. The database servers are not accessible directly by the user. Organizations can easily enforce whatever rules or policies they want on the database server by separating the database and application servers.
Advantages
a) If the application contains a vulnerability, the attacker will not be able to gain control of the database in the first place.
b) Since the database is generated as a different entity, data processing would be very efficient.
2. Identity Access Management (IAM)
We’re all familiar with IAM, which is very powerful in enforcing access management policies, restricting user access for those who don’t have a business need to access the data, and managing the authorization of people/resources.
To make databases more secure, organizations constantly need to reduce the number of users who can access the database.
How to implement IAM?
- IAM’s basic principle is that applying “least privilege” means always providing those rights needed by a user to perform his/her duty.
- Determine the number of individuals who need access to the data and how many need administrative privileges.
- At least two persons should have admin powers, and any changes made by one must be accepted by the other so that no one can abuse their privileges.
- Separation of duties must be made mandatory.
Advantages:
- Using the conventional method as a foundation to make it simple to comprehend.
- Proper identity management gives businesses greater control over user access and lowers the risk of a data breach.
3. Data Encryption
Encryption of data can take place both at rest and in transit.
- Transit encryption: Transit encryption can be handled by implementing SSL (443) using an SSL certificate.
- Encryption at rest: Encryption is the process of converting data into a secret code that only designated individuals can read. This is possible with the use of a public and private key pair. So, before storing the data, encrypt it with a public key so that only the user with the appropriate private key can read it.
Advantages:
a) Encryption always maintains the integrity of the data.
b) Encryption safeguards the user’s privacy because all personally identifiable information (PII) such as credit card numbers and passwords are stored in the database after encryption.
4. Data Masking
Data masking should be used when showing data to the public or users who don’t have a business need to know. Let’s suppose we have the card data of users. Instead of showing the complete data to users each and every time, you should show only the last four digits, which is enough. Data masking should be applied to every piece of sensitive data before displaying it in the public domain or to internal users.
Advantages:
a) You can preserve sensitive data while there is no need for it.
b) It saves organization data from exfiltration, data loss (such as deletion happening during testing), or internal threats.
5. Log Management and Monitoring of Traffic
It is vital to manage the logs of any app or database. Observing log patterns can provide us with information like:
- What are the locations from which the server is getting hits?
- Which IP address is used for accessing our server?
- Which country has the most traffic on the server?
Based on old log patterns, we can then create rules in SIEM tools. If anything wrong gets detected, a warning should be issued. We can thus create and implement network policies based on those rules to save the server from attackers.
Therefore, it is essential to monitor the organization server periodically.
Advantages
a) Log management enables businesses to keep track of their users’ activities and discourage intruders.
b) A log’s aim is to serve as a warning sign when something bad is happening.
6. Use of Firewalls
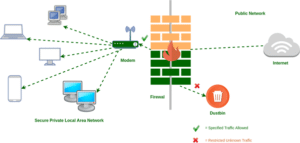
Organizations can use firewalls to protect the database server from external networks. We have two firewalls of this kind.
- Network firewall: The transportation safety layers of these firewalls work. By default, if a firewall admin wants to give permission rights to a user, they can open the firewall ports.
IP-based whitelisting should be applied so that only specific IPs can access the database. Only particular users can access the database server.
- Web application firewall (WAF): This firewall type works on the application layer and can filter internal traffic. Here we can create a signature to detect attacks such as SQLi, XSS, and LFI.
This allows us to protect the database server on two layers.
Advantages
a) SQLi and XSS attacks can be detected and prevented using firewalls.
b) A firewall may be used to prevent unwanted attempts to scan the network for open ports.
7. Using 2FA
2FA means “two-factor authentication”. Once credentials have been inserted, the user must enter a code to access the application or server’s home screen. It thus adds a protective layer.
A strong password is always recommended. A strong password protects your data, but today, companies want to use the 2FA functionality to protect sensitive information even when a password has been compromised. Obtaining account access after introducing 2FA needs more than just a username and password.
With 2FA, attackers need access to the computer (such as a cell phone, email, or RSA token) where users have set up the 2FA to get access. 2FA is an authentication process that duly authenticates the user, limiting data access but does not protect the data itself.
Advantages
a) Implementing two-factor authentication allows employees to securely access corporate systems from any device or location – without jeopardising sensitive data.
b) It adds an additional layer of authentication, preventing unauthorised access to your account if your username and password have been compromised.





