Authentication is a process of validating the identity of a user. It merely has two return values, i.e., true or false. Most authentications will be placed at the start of the system because validation is most important for any system. The system lets you enter if you’re authenticated. Authentication may vary from system to system, but everybody needs some tangible steps to make it most secure.
There are two main steps in authentication: first is the identification, and the second is the central authentication. In the first step, the actual user’s identity is provided in user ID and validation. However, just because the first step is successful, doesn’t mean that the user have been authenticated. In the second step, the user passes their actual credential that only the authenticated user knew.
Common Secure Authentication Methods
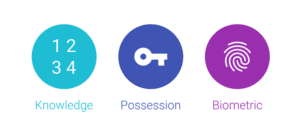
A hacker will always find a way to break a system’s authentication. Security teams need to identify it and secure it or try the next more secure method for prevention. Here is a list of authentication methods that are used to create a secure system:
1. Password authentication
This is the most common and widely used auth process. A password is a user-created string with alphanumeric values with some special characters; it is only known by the person who generates it. A password is also the least secure and most commonly breakable authentication. As you can imagine, many users use many different accounts but often use the same password for all. If one system is compromised, a hacker may get all your accounts at once. So, a password is not sufficient to secure all your private data.
As a security measure, the system can generate a random 16 digit password for a user or ask the user to make a strong password with at least two special characters and alphanumeric values. The system can verify the generated password that will it be strong enough to prevent brute-force. Some steps to make the most secure password:
- Make it long (at least 12-16 characters long)
- Don’t use common phrases ( like iloveyou, iamabc, 1234567890)
- Use alphanumeric and special characters
- Avoid using common terms (like your name, your address, your favorite color)
- Don’t use sequential letters (like qwerty)
2. Multi-factor authentication
As the name indicates, multi-factor authentication uses two or more ways to identify a user, like entering a password AND an OTP sent to the user’s phone or email. It adds another layer of security on top of password authentication. If a hacker can’t pass even one level, the system kicks them out.
If any system has at least two factors, it is more secure as hackers need a lot more details to break into a user’s system or profile. Let’s say one system has two-factor authorization, where one is password and the second is phone notification confirmation. By any chance, if a hacker hacked a systems’ database then he gets the user’s password. As soon as he tried to enter into the system he gets success in the first step, but for the second step, a push notification will be sent to the user. At that time he failed. So, having user interaction during auth process is much needed.
3. Biometric authentication
Biometric authentication is the most secure authentication because it uses the user’s unique biological characteristics. A system uses this auth process if it needs more security. It is widely used at nuclear companies, airports, military bases, etc.
Here are the advantages to use biometric authentication:
- It depends on the user’s unique biology, so the chances of hacking are very low
- You can combine biometrics in a multi-factor auth process.
- You can also put biometric identification checkpoints at a physical entrance where you need the most security, like an airport or a private room/building.
Here are some popular biometric methods:
Facial recognition
As the name states, a user must register their face to gain access. The system stores a person’s facial points against their name, making it easy to identify users during authentication. It is used very commonly by phones. However, this involves many challenges, like low light recognition, recognizing a face from a different angle, faces with or without spectacles or makeup.
Fingerprint scanners
Every user has a unique fingerprint, and it’s the biggest advantage of the authentication process. Currently, it’s the most popular auth for biometrics. A user can register multiple fingerprints as it can help when the scanner cannot recognize the first fingerprint; the user can use a different finger.
Voice Identification
Similar to a password, with voice identification a user needs to register their voice and a key sentence to identify themselves. The system recognizes the user’s voice and inflection, allowing them access. Voice authorization has several advantages: it can be used by cellphones because nowadays every mobile has a microphone, thereby making the authorization process easy and contactless. This method does have its disadvantages as well; it isn’t idle for crowded, noisy places, and may not be as accurate as other biometric data.
4. Certificate-based authentication
Generally, for certificate-based authentication, the system will generate a digital certificate to validate the user. It can be generated from the user’s unique Id like voter ID, passport, or other. It contains the user’s public key and digital signature, with this system will identify the right user, A system takes a digital sign from a user and uses cryptography to make sure it’s a valid user.
5. Token-based authentication
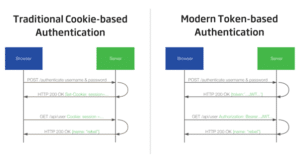
Token-based authentication is a process in which users identify with a unique tokens after the user provides credentials to the system. A token is valid only for a designated time period, after that user needs to re-generate it to use again.
Let’s see how it works.
Step 1: User provides their credentials
Step 2: Server verifies those details, if it verified then it generates a token based on that information of some time.
Step 3: Token sent back to the user
Step 4: Now when the user accesses the system, the system simply asks for the token, if it is valid then the system lets the user proceed further.
Step 5: After the token expires or the user logout, the token got destroyed.
A system will ask for a token when it needs to validate the user, even the user enters the system. So it’s better than traditional password-based authentication.
How to Secure Your Authentication?
As you know there are multiple authentication steps that can be implemented in a system. Implementation is an easy job, but to make it secure makes it a little bit complex. Let’s understand that one by one.
Keep user credential secure
When a user enters their credentials then it sends to the server for verification. At a middle path from the client to the server, an attacker can get those details. To make it secure using some default mechanism,
- First encrypts all inputs then send.
- Use HTTPS protocol for login/registration
- use POST method to send it to the server
Prevent brute-force attack
Brute-force is a mechanism in which an attacker will constantly checking login combinations. For example, if an attacker knows your username is abcqwe and the password is 4 characters long. So, he can try 0000, 0001 … abc1, zzzz until he gets success.
The most effective way to block this attack is to do IP base request parsing. If a request comes from the same source multiple times within the same time frame then block that request. Also, you can check one user can’t enter more than 3 wrong passwords within a set interval.
Double checks on your authentication logic
Before making it live, make sure the authentication process works smoothly. In the authentication process, you can’t expect to have bugs or any backdoors.
Why Is Secure Authentication Important?
Authentication is a must but making it more secure is an addition to security checks. Secure authentication prevents several attacks, that can exploit a system or user data. Having a secure authentication process will make it more difficult for an attacker to gain access to the system.
Only one authentication will not work nowadays. Like system can’t just rely on password authentication. There have been several attacks in which attackers get million of user’s passwords. If your system is having only password auth then you can imagine how easy to get into it if these kinda attacks happen. Multi-factor auth with biometric is the best secure authentication any system can have.
User can trust a system
When you provide data security and privacy, users can trust your system. User depends on the security mechanism of a system. If your system gets hack multiple times, you may lose potential customers. Users will accept complex authentication to protect their data. A system can always protect data by providing security updates.
One thing that you need to remember is while providing secure authentication using multi-factor, the process of that will be less stressful. Users need to complete flawlessly. As you know, you just can’t rely on password auth. There are many rules to make your password strong, at the same time it will also useful for attackers to crack it.
Conclusion
As you know day by day system needs to keep updating the auth process in order to make it solid and unbreakable. On passing each day a hacker finds a new way to breach the authentication of a system, so for a system rather than a password, it needs much more steps to make it secure. Like you know authentication like face ID will reduce the use of a complex password. If your auth is most secure then the attacker won’t get your personal data and won’t breach your system either.





