Encryption is a process by which you can turn your data into something that can not be read by an unauthorized person, which is usually a hacker. To make a system secure, you need to encrypt the data as well as the database. It is difficult to read encrypted data so there’s very little chance that an unauthorized person can understand it. Let’s first understand data encryption.
Data Encryption
Encrypted data is ciphertext and decrypted data is plain text. Ciphertext can only be read by someone who is authorized to have access to it or who has the key to decrypt it. Nowadays, encryption is the best way to secure any service/system.
Types of Data Encryption
There are 2 main types of data encryption—symmetric key encryption and asymmetric key encryption
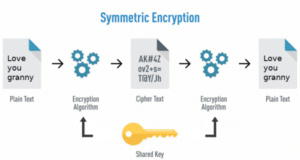
In symmetric key encryption, there is only one key to encrypt and decrypt the message. Both the sender and receiver use the same key for encryption and decryption. This type of encryption is useful if you are building a small system.
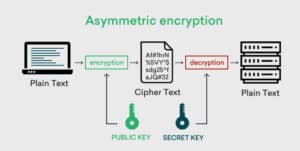
Asymmetric key encryption uses two keys to secure the data. The sender encodes the message using the receiver’s public key and the receiver decrypts the message using their own private key. For this reason, asymmetric key encryption is also knows as public-key encryption. If a system needs to be more secure, then it should be secured using an asymmetric key encryption.
Symmetric key encryption is faster than asymmetric key encryption for two reasons. The first is that symmetric key encryption requires only one key throughout the process and the second is that the asymmetric key encryption process requires the organizer to exchange keys between users.
These are the 2 main types of data encryption but, using the same concept, there are a few different methods available for encryption. Each data encryption method has its own standard. Let’s take a look at some common encryption methods.
Data Encryption Standard (DES)
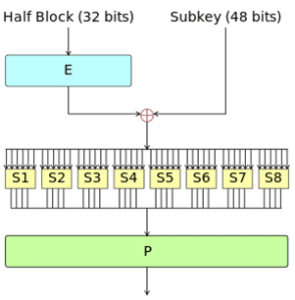
DES is a symmetric-key block encryption method. The block size for DES is 64 bits, which means that 64 bits will be the input for DES and 64 bits ciphertext will be the output of DES. DES can be quite vulnerable to a powerful attack.
Triple DES (3DES)
3DES is a symmetric-key block cypher that overcomes the vulnerability of DES by using a 3 step system: encryption, decryption and encryption again. So, in the end, the block size is 168 bits. Thus, it’s more difficult to hack, but it requires a solid system to perform 3DES encryption.
RSA (Rivest–Shamir–Adleman)
RSA is an asymmetric encryption method that is widely used because of its security. Rivest, Shamir and Adleman are three scientists who invented this method. RSA’s public key is very secure because it is based on 3 main values, 2 prime numbers and 1 random number.
Advanced Encryption Standard (AES)
AES is a symmetric encryption method that is most useful because it is six times faster than 3DES. AES is mainly based on a substitution-permutation network. The main features of AES are that it uses 28/192/256-bit keys to encrypt and decrypt messages, it is an easily available software for key generation and it is stronger than 3DES.
Secure Socket Layer (SSL)
The main use of SSL is to encrypt data in transit. It encrypts data just before it is written on a disk or it sent to the server. The “s” in “https://” and the lock icon in the browser’s URL is a sign of SSL.
End-to-end encryption (E2EE)
E2EE means nobody can access data while it’s in a communication channel. When one sends data, it is encrypted before transferring to the receiver and that data can only be decrypted by the receiver. So, if a hacker breaches your server or an internet service provider (ISP) tries to access your data, they simply won’t be able to read it.
Implementing Data Encryption
Let’s take a look at how data encryption works. In this example, I’m using Javascript with NodeJS. NodeJS is a server side language that has many built-in methods and modules to perform data encryption.
This way you can do simple encryption. If anyone gets the message in transit, they won’t be able to understand it because it is encrypted.
Database encryption
Like data, you can also encrypt the database. The database encryption process uses a specific algorithm to convert data into ciphertext. The main purpose of database encryption is to protect stored data. Therefore, if a hacker gets all the data, they won’t be able to understand it. This also reduces the chances of hacking because encrypted data is of no use to attackers.
Types of database encryption
Database encryption depends on the encryption target. Choosing a target depends on the system. Let’s understand encryption targets:
Column-level encryption
In column-level encryption, individual columns of data are encrypted. This method works even if there is more than one column. All the encrypted columns have the same encryption and decryption key. This method is best when you have a small system and you want to encrypt only user credentials. So, for example, you can encrypt three columns—username, email and password.
Row-level encryption
Like the name suggests, in row-level encryption, individual rows of data are encrypted. After encryption, each row is identified by a primary key. This method is particularly useful when you want to encrypt specific sets of data.
File-level encryption
Sometimes a database needs to protect unauthorized persons from reading and accessing confidential files. If the database has a file storing mechanism then it needs to be encrypted before storing. This is referred to as file-level encryption.
Full data encryption
As the name suggests, full data encryption encrypts everything—plain text, files, images, videos etc. It’s the best and most effective database encryption method. If a hacker accesses any data, he gets encrypted data only. Basically, it secures the whole database.
In order to better understand database encryption, let’s look at an example of column-level encryption. The example below is from the MySQL database. The MySQL database has some default encryption and decryption functions that are ready to use. You can take it one step further and encrypt access user’s password as well by simply using the query below:
INSERT INTO users (username, password) VALUES (‘root’, AES_ENCRYPT(‘PASSWORD@!@#’, ‘encKey’));
So, your password ‘PASSWORD@!@#‘ is encrypted before storing into your table. When sending it to a user you need to decrypt it using the same key i.e encKey
SELECT AES_DECRYPT(password, ‘encKey’) FROM users WHERE username = ‘root’;
To implement data encryption using MySQL you need to have SSL connection to the database.
Benefits of Data and Database Encryption
Hacking is a big problem for all systems. Making your data secure provides more benefits to your system. Some benefits of data encryption are explained below.
Data is protected
Complete encryption protects data in any state. A hacker can attack anywhere, along a communication channel or where data is stored. Once you send, receive and store encrypted data, it prevents the risk of your data being exposed. A hacker might take this data and perform brute-force attacks to uncover the raw data but the process will take a lot more time.
Data can be sent securely
Data is at its most vulnerable when it is in transit. Therefore, you should start encoding data and use SSL/TSL to send it. This gives you the surety that your data is protected at any point in time. Also, you should encode files before sharing them online. If you store data in encoded form then you no longer need to encode it before sending. This will save time and make request/response faster.
Data integrity is assured
Sometimes, we worry: if I encrypt my data will it remain as it is? The answer is yes. Encryption only turns plain text into ciphertext, it doesn’t change the meaning of the data. Nowadays, data stealing is a huge issue faced in every system. If a hacker tries to change your data, then the sender immediately knows that the data has been tempered with. So, it’s easy to track and fix.
Conclusion
Data privacy is a real concern for a secure system. To protect data a system needs to perform data encryption. Make sure that your system sends only encrypted data over a communication channel and also stores data in encrypted form only. Encrypted data can only read by the sender and their elected receivers.





