Before diving into E2E encryption, let’s recap the basics. The encryption process simply turns your readable and understandable data into something that can not be read or understood by someone who doesn’t have the decryption key, making your data secure. The foundational concept of encryption is the key that will help decode encrypted data, making it readable. This is the most effective way to keep your data secure.
What is End-to-End (E2E) Encryption?
End-to-end encryption means nobody can access data while it’s in a communication channel. When one sends data, it will be encrypted before transferring to the receiver so that only the receiver can decrypt data. So, if a hacker breaches your server or an Internet Service Provider (ISP) tries to access your data, they simply won’t be able to read it.
The most critical place where data can be hacked is when it’s within the communication channel. However, encryption solves this easily as encrypted data in a communication channel, if intercepted, cannot be read. This is why end-to-end encryption is a must to secure data.
How Does E2EE Work?
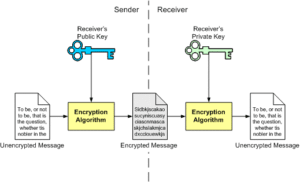
Encryption and decryption processes depend on cryptographic keys. These keys are stored at the sender and receiver’s devices (also known as endpoints) so that nobody else can get them. There is an algorithm on a user’s device that can mathematically generate two cryptographic keys, simply known as a public key and a private key.
With the public key, anyone can encrypt messages, and with the private key, anyone can decrypt messages. So for the sender, there is one public key, and for the receiver, there is one private key. If the communication is two-way, then this applies vice-versa as well. Exchanging these keys allows for messages to be secure in transit and still readable when they reach their endpoints.
Let’s look at an example to illustrate this better.
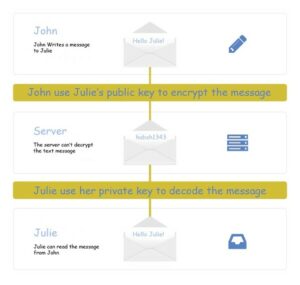
Suppose John wants to send a message to Julie using a secure medium. For that, John must use Julie’s public key to encrypt the message. So, John will first encrypt his message and then send it through an open communication channel, which may include multiple routes, servers, or paths.
Now, let’s assume a service provider wants to read the message that’s being passed. Because of the E2E encryption, they won’t be able to read it as they don’t have the required private key to decrypt it. Therefore, only Julie can read the message as she holds the private key. The same process applies when Julie wants to reply and send a message to John; she will encrypt her message using John’s public key.
Let’s dive into a real example for better understanding.
Generating a Public/Private Key Pair
You can follow the steps below to generate a public and private key. For additional options, check ssh-keygen.
1. Open the terminal and start the program:
Your terminal: ssh-keygen
> Generating public/private rsa key pair.
> Enter file in which to save the key (/home/julie/.ssh/id_rsa):
2. Now you need to enter a file path.
As you see, by default, the name of the file is id_rsa, which has your key. You can select this file by pressing Enter unless you want to use a different filename.
Enter file in which to save the key(/home/julie/.ssh/id_rsa): <Return>
So, a public key is created, and the string .pub is appended to the private key.
3.You can also add a passphrase or password for your key.
Enter passphrase(empty for no passphrase): <Type the passphrase>
4. In the next step, it will ask you to enter it again.
Enter same passphrase again: <Type the passphrase>
Your identification has been saved in /home/julie/.ssh/id_rsa.
Your public key has been saved in /home/julie/.ssh/id_rsa.pub.
The key fingerprint is:
0e:fb:3d:57:71:73:bf:58:b8:eb:f3:a3:aa:df:e0:d1 julie@myLocalHost
5. Your key is generated successfully; you can check it by looking at path home/julie/.ssh/id_rsa.pub
Now Julie will share her public key with John. Let’s name Julie’s public key pub_key_julie. Similarly, John will share his public key named pub_key_john. Thus, the main requirement of communication is fulfilled. Now John will encrypt his messages with the private key pub_key_julie and send that over a channel. As soon as Julie receives the message, she will decrypt it with her private key pri_key_julie.
This way, you can enable an E2E encryption process.
Challenges with End-to-End Encryption
There are risks and challenges involved with all types of security measures. Let’s look at the challenges with end-to-end encryption.
Man-in-the-Middle (MitM) attacks
This is the most performed attack in end-to-end encryption. As we know, attackers can’t access data when it’s in the transfer process. What they do instead is change the recipient’s data during the key exchange or substitute their public key for the recipient’s.
Let’s understand a MitM attack by extending our earlier example.
Assume that Julie’s generated private key is asd123. If Julie sends this key to John through an insecure server, a hacker may intercept it. They can then simply change the key from asd123 to qwe123 and send it back. Now Julie and the hacker both have the same private key. Through this, the hacker can read all of Julie’s messages, resulting in data breaches.
Endpoint security
As you know, cryptographic keys are stored at the user’s end. So, they need much more security against attackers. A user’s device can be easily hacked for the public/private key. Once a hacker gets those keys, it’s straightforward to perform a MitM attack. A hacker can also hack the decrypted data at the user’s end via a public key or log files. So, it’s imperative to make the endpoint as secure as possible with isolate key generation, storage, and cryptographic operations.
Backdoors
A backdoor is a vulnerable place in your system from where an attacker can bypass your security. For end-to-end encryption, you must take care of all the backdoors so that nobody can get the decrypted data.
Pros and Cons Of E2E Encryption
There are several pros of end-to-end encryption over standard encryption.
Pros:
- Easy Integration: E2E encryption method can be easily integrated with an existing system. For this to function, one just needs to add an encryption/decryption layer to it.
- Extremely secure: The basis of this system is the idea of cryptographic keys. As only the sender and receiver have the correct keys, a hacker cannot access messages or modify them in any way. Even web servers and ISPs cannot read your data.
Cons:
- Extreme Vigilance: If a system uses the public-private key concept, then the exchanging of keys also needs to be secure. If something is misplaced, then a MitM attack can happen. So apart from generating secure keys, sending them securely is also an important task.
- Storing a key: Generating and storing keys at the user end is a bit difficult and risky. If a user’s device gets hacked, then the hacker can control the cyphertext. So, the keys have to be stored so that they cannot be accessed even if your system is compromised.
Conclusion
End-to-end encryption is an extremely secure method for data security. Only the sender and its elected receivers can read messages, plus it’s straightforward to integrate with the current system. However, a system owner needs to take care of some edge cases.






