Session management manages sessions between the web application and the users. The communication between a web browser and a website is usually done over HTTP or HTTPS. When a user visits a website, a session is made containing multiple requests and responses over HTTP.
According to RFC (section 5, RFC2616), HTTP is a stateless protocol. In this process, each request and response is independent of other web processes. Session management capabilities linked to authentication, access, control, and authorization are commonly available in a web application.


Source: OWASP
Modern web applications require maintaining multiple sessions of different users over a time frame in case of numerous requests. Regarding security, session management relates to securing and managing multiple users’ sessions against their request. In most cases, a session is initiated when a user supplies an authentication such as a password. A web application makes use of a session after a user has supplied the authentication key or password. Based on the authentication, the user is then provisioned to access specific resources on the application.
Session ID
A session ID, also known as a session token, is a unique number ID assigned by a website server to a specific user for the duration the user is on the website. This session ID’s storage is in the form of a cookie, form field, or URL. Each time a user opens a web browser and visits a website, a session ID is generated. The session ID remains the same for some time. If a user closes the browser and reopens the web browser to visit a site, a new session ID is created again.
The token or session ID binds the user’s credentials for authentication for user HTTP traffic. The web application then applies the access control and permissions.
Session Cookies
A session cookie contains data put away in a temporary memory area and deleted after the session is finished or the web browser is closed. This cookie stores data that the client has entered and tracks the client’s developments inside the website. This kind of cookie is made without a set date, unlike a persistent cookie, which has an expiration date attached to it. Since a session cookie is temporary, it doesn’t acquire data from the user’s PC or the user’s identity.

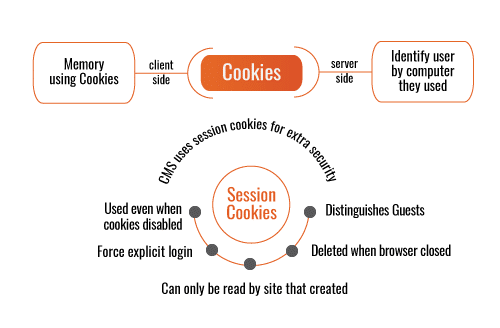
Source: Composr
Attacks related to Sessions
When authentication and session management are not properly secured and configured, adversaries can steal the passwords or session IDs to access user’s accounts and spoof their IDs. If the session IDs are compromised, adversaries can impersonate other users on the network, system, or application. This kind of attack is known as session hijacking, where the hacker can use brute force, predict and expose the session tokens.
Session fixation is another type of attack that enables attackers to hijack a user’s valid session ID.

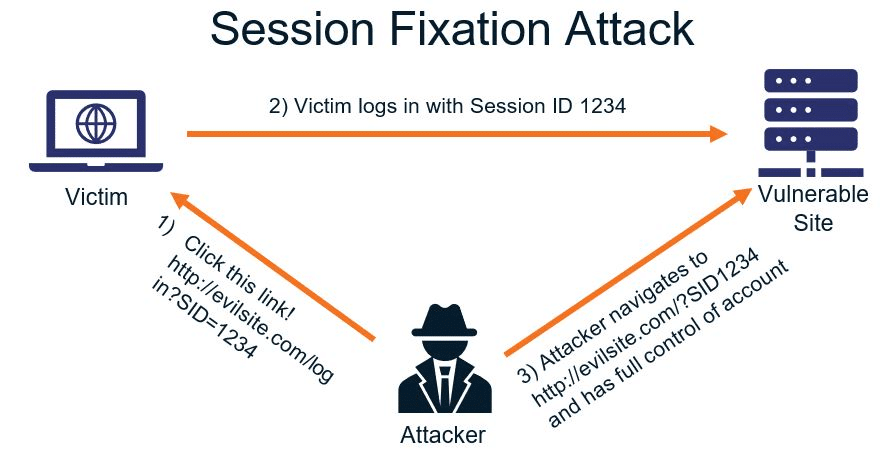
Source: Security Boulevard
According to Acunetix, “The attack explores a limitation in the way the web application manages the session ID, more specifically the vulnerable web application. When authenticating a user, it doesn’t assign a new session ID, making it possible to use an existent session ID. The attack consists of inducing a user to authenticate himself with a known session ID and then hijacking the user-validated session with the knowledge of the used session ID. The attacker has to provide a legitimate web application session ID and try to make the victim’s browser use it.”
Best Practices for Implementing Session Management
Having many points of attack related to a web session or a large attack surface can compromise web applications and sessions in many different ways.
Below are some of the best practices for implementing session management. Implementing these practices will reduce the attack surface and minimize the risk and damage caused by vulnerabilities and attacks resulting from improper session management.
- Setting secure HTTP flags on cookies
Avoid sending sensitive traffic over unencrypted channels, i.e. HTTP. Setup the secure flag, which will ensure that data is transmitted over encrypted protocols such as HTTPS. The HTTP flag should only be set on session cookies to prevent session hijacking, which can be caused due to client-side javascript execution.
- Generation of new session cookies
New session token generation should be ensured at every step of the authentication and interaction process, i.e. when a user visits an application or website and when the user gets authenticated. Apart from this, a new session should be created when a user exits from the application. Cookies should have an expiration time. In this way, if an account is inactive for a long time the session will expire.
- Session cookies configuration
Session tokens should not be easily guessable, they should be long, unique and unpredictable. Doing so will decrease the chances of an attacker being successful in using brute force to figure out the session token. The expiration time of persistent cookies should be no longer than 30 minutes, so that attacks such as session fixation can be prevented.
Session Management Best practices according to OWASP
The following are some of the best practices as per the OWASP
- Use a trusted server for creating session identifiers.
- Efficient algorithms should be used by the session management controls to ensure the random generation of session identifiers.
- Ensure that the logging out functionality terminates the associated connection/session entirely.
- Ensure that session inactivity timeout is as short as possible, it is recommended that the timeout of the session activity should be less than several hours.
- Generate a new session identifier when a user re-authenticates or opens a new browser session.
- Implement periodic termination of sessions, especially for applications that provide critical services.
- Appropriate access controls should be implemented to protect all server-side session data from unauthorized access by other users.
Conclusion
Session management control and implementation should be taken seriously by organizations that provide critical services locally or globally. Software developers should implement best practices for all session management to evade threats and attacks that can compromise the confidentiality, integrity and availability of their applications and web services.





