By Avi Douglen
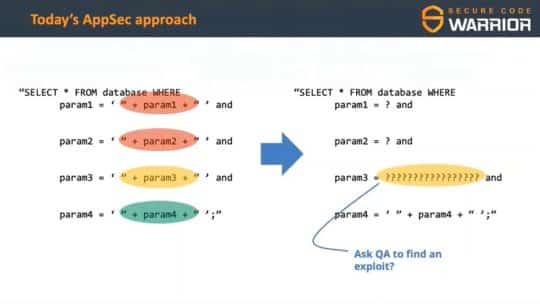
We’ve all been there – we’ve each spent too much time and resources on security, but 3 months later we still get breached anyway. “But we followed all the ‘Best Practices’!” your developers cry.
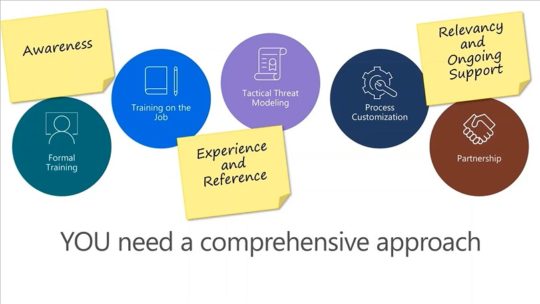
In this flash intro to secure software design, AviD will show why every software development process should start with Threat Modeling, and how to efficiently get security to contribute to the bottom line.